SANS Cyber Safari 2024
Sat, Oct 5 – Thu, Oct 24, 2024
Hands-On Cyber Security Training in Riyadh
Unlock the full potential of your career with cyber security training at SANS Cyber Safari 2024 (October 5-24). Guided by world-renowned instructors at the forefront of the field, this event provides exclusive access to live industry experts, ensuring you stay ahead of the curve.
Immerse yourself in a learning environment that features industry-leading hands-on labs, simulations, and exercises, all geared towards practical application in your professional endeavors. Seize the opportunity to hone your skills during bonus sessions and activities, backed by SANS unwavering commitment to excellence and expertise.
SANS Cyber Safari 2024 Features
- Practical Cyber Security Training: Delivered by real-world practitioners providing actionable insights.
- Real-time Support: Receive immediate assistance from certified teacher assistants throughout your course.
- Immersive Labs in a Virtual Environment: Hands-on practice to sharpen your skills in a secure setting.
- Thought Leadership Talks & Workshops: all centered around training topics.
- Comprehensive Courseware: Course materials provided in electronic and printed formats.
- GIAC Certification: Most courses align with the highest standard in cybersecurity certification.
- CPE Credits: Earn Continuing Professional Education credits towards a certification.
Whether you’re a seasoned professional or new to the field, SANS Cyber Safari 2024 equips you with the skills and knowledge needed to navigate the ever-evolving threat landscape.
Please note, courses are available In-Person in Riyadh, SA and Live Online during this event. Register now to secure your spot.

Courses are offered In-Person or Live Online.
Please see available courses for details regarding individual course delivery format.
SEC401: Security Essentials - Network, Endpoint, and Cloud
$8,645 USD
* Times include breaks
* Times include breaks
SEC504: Hacker Tools, Techniques, and Incident Handling
$8,645 USD
* Times include breaks
* Times include breaks
FOR578: Cyber Threat Intelligence
$8,645 USD
* Times include breaks
* Times include breaks
SEC497: Practical Open-Source Intelligence (OSINT)
$8,645 USD
* Times include breaks
* Times include breaks
SEC488: Cloud Security Essentials
$8,645 USD
* Times include breaks
* Times include breaks
LDR514: Security Strategic Planning, Policy, and Leadership
$8,135 USD
* Times include breaks
* Times include breaks
SEC530: Defensible Security Architecture and Engineering: Implementing Zero Trust for the Hybrid Enterprise
$8,645 USD
* Times include breaks
* Times include breaks
GDSA: GIAC Defensible Security Architecture
$8,645 USD
* Times include breaks
* Times include breaks
SEC450: Blue Team Fundamentals: Security Operations and Analysis
$8,645 USD
* Times include breaks
* Times include breaks
SEC565: Red Team Operations and Adversary Emulation
$8,645 USD
* Times include breaks
* Times include breaks
SEC542: Web App Penetration Testing and Ethical Hacking
$8,645 USD
* Times include breaks
* Times include breaks
SEC511: Continuous Monitoring and Security Operations
$8,645 USD
* Times include breaks
* Times include breaks
FOR572: Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response
$8,645 USD
* Times include breaks
* Times include breaks
Cyber ranges
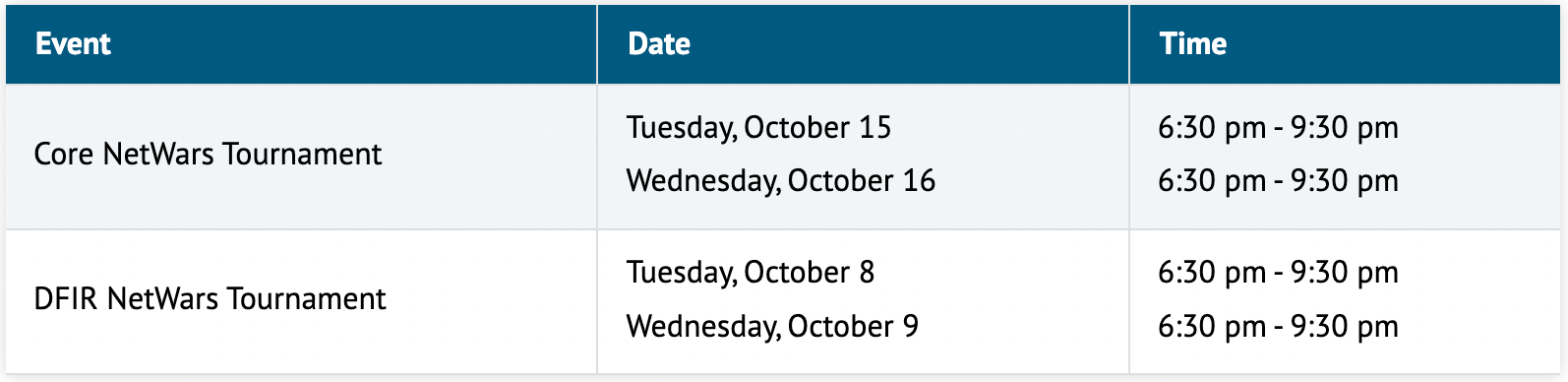
Tournament: Core NetWars
Registration: All students who register for a 4-6 day course will be eligible to play NetWars for free. Registration for this event will be through your SANS Account Dashboard the week of the event.
About Core NetWars: The most comprehensive of the NetWars ranges, this ultimate multi-disciplinary cyber range powers up the most diverse cyber skills. This range is ideal for advancing your cybersecurity prowess in today’s dynamic threat landscape. The winning team and the top five solo players from every Core NetWars tournament throughout the year are offered a chance to compete in the annual SANS Core NetWars Tournament of Champions.
Computer Requirements: Browser-based
- Chrome, Firefox, Safari, or Edge browsers
- 8GB of RAM
Recommended For: All infosec practitioners of any level. It is recommended, but not required, that students have a basic or foundational knowledge of information technology and technical topics.
Disciplines: Cybersecurity 101, Cyber Defense, Penetration Testing, Digital Forensics, Incident Response, Cloud Computing.
Example Topics:
- Hardware hacking
- Mobile app analysis
- Nerd trivia
- Threat hunting with ELK Stack
- Web application pentesting, including GraphQL
- Linux and Windows command line skills, including PowerShell, cURL, and jq
- Windows, web server, and network forensics
- Cyber threat intelligence
- Cryptography
- Cloud penetration testing
Interactive Scenario: Some SANS students are relaxing at a local arcade after a long day learning elite new cyber skills. All of a sudden, they’re pulled into a digital world ruled by an AI! Is it benevolent? Will they escape? Will they make it back in time for class tomorrow?
Tournament: DFIR NetWars
Attendance Options: In-Person and Live Online
Registration: All students who register for a 4-6 day course will be eligible to play NetWars for free. Registration for this event will be through your SANS Account Dashboard the week of the event.
About DFIR NetWars: Focused on digital forensics, incident response, threat hunting, and malware analysis, this tool-agnostic approach covers everything from low-level artifacts to high-level behavioral observations.
Computer Requirements: Laptop/desktop-based
- Processor: 64-bit, x86, 2.0 GHz+
- Memory: 16GB (8GB is possible with reduced performance)
- HD: 200GB+ Free, and approximately 50GB download of evidence files and virtual machines
- Interface: USB 3.0 | Type-A or dongle with Type-A
- Operating System: Windows 10 or later, Mac OS 10.15 or later, Linux
- Virtualization Software: VMware – Students are expected to either provide their own forensics tools or use the local VMware VM tools that we provide.
- Extra Requirements: Files downloads are required to participate.
Recommended For: Experienced Digital Forensic Analysts, Forensic Examiners, Media Exploitation Examiners, Malware Analysts, Incident Responders, Threat Hunters, Security Operations Center (SOC) Analysts, Law Enforcement Officers, Federal Agents, Detectives, and Cyber Crime Investigators.
Disciplines: Digital Forensics, Incident Response.
Example Topics:
- Threat Hunting
- Malware Analysis
- SIFT Workstation
- Media Exploitation
- Artifact Analysis
- Rapid Triage
- Malicious attacks
- Network traffic analysis
- Reverse engineering and debugging
- Intrusion detection
Interactive Scenario: As a DFIR specialist, you are provided with evidence files from a series of mysterious compromised systems and conventional computing environments. Your mission? Use your DFIR skills to shed light on attack vectors, indicators of compromise, and other evidence needed to resolve the incident.

SANS Summits

